Russian Cyber Attacks
Russia’s cyber attacks on the United States and elsewhere are ongoing. Russian criminals and intelligence officials collaborate to mine data and steal information, hacking U.S. banks, governments, and hospitals.
In addition to stealing proprietary emails and documents and strategically leaking them online during the 2016 presidential campaign, Russian cybercriminals breached election-related computer systems in at least 21 states. Russian hackers also are proving they have the capability to access critical infrastructure like power and nuclear plants.
Recently, the computer-security firm Symantec warned that a cyber espionage group called Dragonfly had reemerged and was behind cyber breaches at about 100 power companies and nuclear plant operators since the beginning of 2017. Half of those were in the United States.
On August 22, 2017, President Trump’s cybersecurity coordinator Rob Joyce told CBS News the United States’ cybersecurity defense force is understaffed by about 300,000.

2004
Operation Pawn Storm
Operation Pawn Storm – later named FANCY BEAR by cybersecurity firm Crowdstrike - emerges.

July 26, 2013
Authorities bust Russian credit card hackers
Authorities bust a gang of mostly Russian hackers who stole more than 160 million credit card numbers over eight years, making the scheme the largest cyber-heist in the U.S. to date.

March 6, 2014
US sanctions Russia over Ukraine and Crimea
The United States issues the first of its sanctions on Russia for invading Ukraine and forcing the annexation of Crimea

October 13, 2014
iSight Report
Cybersecurity firm iSight Partners publishes a report explaining how a Russian government-backed hacking group nicknamed Sandworm is exploiting a flaw in Microsoft’s Windows operating system. iSight says Sandworm launched cyber espionage operations against NATO, Poland, Ukraine, the European Union, and specific European telecommunications and energy firms.

October 29, 2014
White House to Washington Post: Hacker Breach
White House officials tell The Washington Post hackers breached the unclassified network of the Executive Office of the President sometime earlier in the month. Sources suspect Russian government sponsored hackers are behind the attack.

November 17, 2014:
State Dept tells Reuters email hacked
The State Department tells Reuters that hackers recently attacked the department’s unclassified email system, which then had to be taken down to improve security. The timing of the State Department attack coincides with the one at the White House. Other US government agencies hacked around the same time include the Office of Personnel Management, the U.S. Postal Service, and the National Oceanic and Atmospheric Administration (NOAA).

March 10, 2015
US officials call State Dept email hack worst ever
US federal officials call the State Department email hack the "worst ever’ cyberattack intrusion against a federal agency.” They suspect Russian hackers are responsible for it as well as the contemporary attacks on the White House and other US federal agencies. Two years later, The Washington Post reports new details about the incident, including confirmation that COZY BEAR was the culprit.

April 8, 2015
TV5Monde Hacked
A massive synchronized cyberattack takes over all of TV5Monde’s 11 TV channels, its social media accounts and websites, and its company email. The global French-language network, which provides 24-hour news and entertainment programming to 260 million homes worldwide, goes dark for four hours before officials regain control. A group calling itself the Islamic State’s “Cyber Caliphate” takes responsibility for the attack, but investigators soon uncover evidence pointing to Russian Intelligence-linked FANCY BEAR using ISIS’ name to cover its tracks. US federal officials call the State Department email hack the "worst ever’ cyberattack intrusion against a federal agency.” They suspect Russian hackers are responsible for it as well as the contemporary attacks on the White House and other US federal agencies. Two years later, The Washington Post reports new details about the incident, including confirmation that COZY BEAR was the culprit.
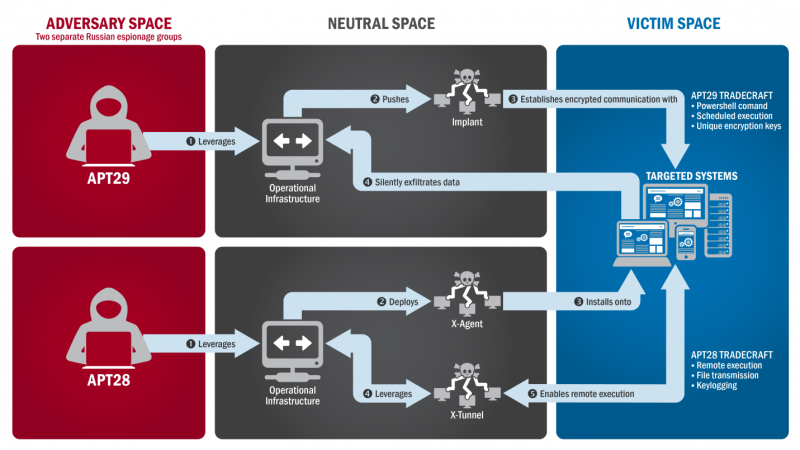
April 8, 2015
The Daily Beast reports increase in Russian cyber activity
Crowdstrike co-founder Dmitri Alperovitch tells The Daily Beast his cybersecurity firm has seen a dramatic increase in Russian cyber activity since the United States imposed sanctions in 2014. Alperovitch points to COZY BEAR and explains the group’s activity is not retaliatory but rather Russia’s attempt to stay globally competitive via cyber espionage.

May 8, 2015
Fancy Bear spies on Bundestag
Hackers spend weeks cyber spying on the German parliament’s computer network. The attack targets digital information from offices of at least 16 people within the Bundestag, including German Chancellor Angela Merkel. Authorities discover FANCY BEAR is responsible, having gained access via spear phishing.

Summer 2015
Attackers infiltrate the DNC network
Attackers use COZY BEAR to infiltrate the Democratic National Committee network undetected and camps out for more than a year spying on internal chats and emails.

July 25, 2015
Russian hackers infiltrate the Pentagon Joint Chief of Staff’s email
Russian hackers use spear phishing to infiltrate the Pentagon Joint Chief of Staff’s unclassified email system, forcing U.S. officials to take it down for nearly two weeks. The shutdown impacts some 4,000 military and civilian personnel.

December 23, 2015
Russian hackers down Ukrainian power grid
A sophisticated, well-coordinated attack that experts attribute to Russian hackers takes down a Ukrainian power grid, leaving close to 250,000 people without electricity.

March 19, 2016
John Podesta email compromised
Hillary Clinton’s campaign Chairman John Podesta clicks on a malicious spear phishing email link, unknowingly giving suspected Russian Intelligence hackers access to his Gmail account.

April 2016
Hackers attack DNC again
Hackers use FANCY BEAR in a second independent attack on the DNC network. The committee’s IT team notices something is wrong and alerts executives who call in Crowdstrike. Crowdstrike identifies two separate hacker groups in the system, FANCY BEAR and COZY BEAR.

June 14, 2016
Media begins reporting on DNC attack
News organizations begin reporting on the DNC attack. The Kremlin denies Russian involvement. The DNC and Crowdstrike believe hackers stole the committee’s entire database of opposition research on Donald Trump but “no financial information or sensitive employee, donor or voter information was accessed by the Russian attackers.”
June 15, 2016
Crowdstrike posts report on DNC hacks
Crowdstrike posts Bears in the Midst: Intrusion into the Democratic National Committee, a detailed explanation of how it believes COZY BEAR and FANCY BEAR hacked the DNC. That same day, someone calling himself Guccifer 2.0 posts on a newly created Wordpress site that he alone is responsible for the hack. He releases what appears to be the stolen Trump opposition research as well as some additional documents and spreadsheets designed to disprove the DNC’s claim it hadn’t lost any sensitive information. Guccifer 2.0 says Wikileaks has the rest of his yield and will be publishing it shortly. Crowdstrike stands by its assessment that Russian operatives are responsible, and other security experts agree, calling Guccifer 2.0 an intentional Russian disinformation campaign.

July 22, 2016
Wikileaks publishes stolen DNC emails
Wikileaks publishes the first wave of tens of thousands of stolen emails and attachments from seven officials at the DNC.

July 28, 2016
Reuters: FBI investigating cyber attack against DCCC
July 28, 2016: Reuters reports the FBI is investigating a cyber attack against the Democratic Congressional Campaign Committee (DCCC), which likely started in March or April but wasn’t discovered until June. Tens of thousands of pages of stolen documents and sensitive information turn up online by August, including “the home addresses, cellphone numbers and personal email addresses of Democratic House members.” Starting in August, Guccifer 2.0 sends information to political bloggers focused on specific House races in key states like Florida, Pennsylvania, New Hampshire, Ohio, Illinois and North Carolina.

September 13, 2016:
DCLeaks posts former Secretary of State Colin Powell emails
DCLeaks posts more than two years’ worth of emails stolen from former Secretary of State Colin Powell’s Gmail account.

October 7, 2016:
DHS statement: Russian government is behind the recent email and computer network hacks
The Department Of Homeland Security and the Office of the Director of National Intelligence on Election Security issue a joint statement saying they are confident the Russian government is behind the recent email and computer network hacks, adding, “[t]hese thefts and disclosures are intended to interfere with the US election process.” It continues: “Some states have also recently seen scanning and probing of their election-related systems, which in most cases originated from servers operated by a Russian company.” However, US Intelligence is not yet prepared to attribute these activities to the Russian government.

October 9, 2016
Wikileaks publishes thousands of Podesta’s stolen emails
Wikileaks starts publishing thousands of John Podesta’s stolen emails including hundreds of attachments.

November 8, 2016
Trump wins election
Donald Trump wins the US Presidential election.

December 22, 2016
Crowdstrike report on Android malware implanted in Ukrainian artillery units
Crowdstrike publishes a report explaining how FANCY BEAR implant malware into Android devices to “track and target Ukrainian artillery units from late 2014 through 2016.” However, both the International Institute for Strategic Studies (IISS) and the Ukrainian Ministry of Defense say the cybersecurity firm’s assessment is wrong because its conclusions rely on misread IISS information. Crowdstrike changes key part of its report three months later but refuses to retract it entirely. The alleged error casts doubt in some circles as to the overall accuracy of Crowdstrike’s previous Russian hacking assessments.

December 29, 2016
President Obama orders sanctions against Russian intelligence services and officials
President Obama orders sanctions against Russian intelligence services and officials, expelling 35 diplomats from the country and shuttering two Russian-owned recreational compounds, one in Maryland and one in New York. The move is in response to Russia’s cyber attacks during the 2016 campaign.

December 31, 2016
Russian hackers breach Burlington Electric
The Washington Post reports Russian hackers got into a computer at Burlington Electric in Vermont. While the hackers did not disrupt operations and the affected laptop was not connected to the grid, the breach shows the true vulnerability of our nation’s electrical systems.

March and April 2017
Wired reports Macron and Merkel phishing targets
According to analysts at Trend Micro as reported by Wired, FANCY BEAR sets up phishing sites aimed at “campaigns of left-leaning politicians Emmanuel Macron and Angela Merkel in upcoming French and German elections.”

May 4, 2017
Macron campaign data leaked days before election
Less than 48 hours before France’s runoff election between Emmanuel Macron and Marine Le Pen, someone anonymously posts 9GB of stolen internal information from the Macron campaign. Capitalizing on rules forbidding candidates from public speaking two days before an election, the data dump appears designed to limit Macron’s defense. Macron wins the election handily. Security firms again recognize the hack to be the work of FANCY BEAR.

May 9, 2017
NSA's Rogers testifies he warned French authorities of suspicious Russian cyberactivity prior to Macron leak
National Security Advisor Mike Rogers testifies before the Senate Armed Services Committee and says he warned French authorities the US was seeing suspicious Russian cyberactivity prior to the Macron leak. Rogers says he asked how his team could help and adds he is doing the same with his counterparts in German and Britain.

May 23, 2017
Qatar’s News Agency hacked
Qatar’s News Agency is hacked. The hacker posts a fake statement attributed to Qatar Sheikh Tamim Bin Hamad al-Thani that flatters Iran and angers Saudi Arabia and other regional allies. The Saudis, the UAE, Bahrain, and Egypt immediately break relations with Qatar, ban its media, and declare a trade and diplomatic boycott, accusing Qatar of supporting terrorism. US intelligence officials believe the UAE is behind the attacks.

June 7, 2017
CNN reports US investigators suspect Russia behind Qatar attacks
CNN reports US investigators now suspect Russia may be behind the Qatar News Agency cyber attack, planting fake information in an effort to cause trouble between the US and its allies.

June 13, 2017
Defense Secretary James Mattis testifies about Russia hacks in Qatar
Defense Secretary James Mattis testifies before the Senate Armed Services Committee and explains what happened in Qatar could be evidence of Russia “trying to break any kind of multilateral alliance ... that is a stabilizing influence in the world.”

August 22, 2017
Trump’s cybersecurity head to CBS: US cyber-defense understaffed
President Trump’s cybersecurity coordinator Rob Joyce tells CBS News the United States’ cybersecurity defense force is understaffed by about 300,000.

September 13, 2017
U.S. Department of Homeland Security bans federal use of Kaspersky software
The U.S. Department of Homeland Security officially bans federal use of software from Kaspersky Lab, a Moscow-based cybersecurity company that U.S. officials believe has ties to the Kremlin and Russian intelligence.
